AWS IAM - Request Action & Request Context
Overview of How AWS IAM works - Authentication & Authorization
This blog is about the overview of how the Identity and Access Management IAM service actually works, and that includes authorization and authentication.

So we have our AWS account and there's a few ways that we can access our account so we can authenticate and then access resources. • The first is the console, the AWS management console. That's the Web based interface. • We've then got the AWS command-line interface - the CLI running commands on a command line • And the application programming interface, the API, where we can authenticate through code.
So when we authenticate to AWS, we do so through the IAM service and all principles must be authenticated to send requests.
So you must authenticate if you're going to perform an action or operation on an AWS resource. Now there are a few exceptions. One example is an S3 bucket, which you can enable for anonymous access.
A principal is a person or an application that can make a request for an action or operation against an AWS resource.
So, for example, these are all principles.
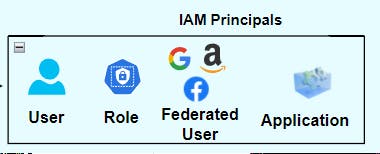
- We have a user
- we have a role
- we have a federated user - a user that has come from another source of the identity provider like Facebook or Google or Amazon for example
- And then we have an application that might be using an user account and it might be using an access key, which is a way that you could authenticate programmatically. It could also be using a role, but it's an application that needs to authenticate using one of those mechanisms.
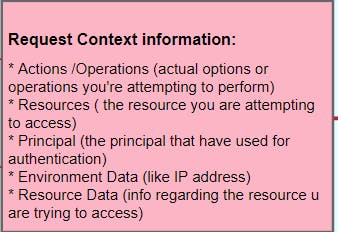
When we attempt to perform an action or operation on an AWS resource, a request context is created. So this means that certain information is put into a context in order to evaluate whether you're going to be authorized to access that resource & able to perform that specific action or operation.
- So this includes the actual actions or operations you're attempting to perform,
- the resources you are attempting to access.
- the principle that you're using that you've used to authenticate and then using to access the resource.
- And some environment data -this can be things like the IP address that you're coming from.
- And also resource data - So information is associated with the resource that you're trying to access.
AWS will then authorize your request. It will either allow or deny the request. And a couple of ways we can control this authorization is through IAM policies. So we have two different types on the screen here.
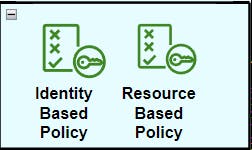
We've got the identity based policy and the resource based policy.
- The identity based policy applies to users and roles
- whereas the resource based policy applies to an actual AWS resource such as an S3 bucket or RDS.
If your request is allowed, then the API action you're running will be executed against the resource. So for example, run instances on EC2, get bucket on S3 or create RDS. (refer the above full diagram)

